aptlab: sharing things publically (ingress)
i've already figured out how to expose services to my tailnet (https://tailscale.com/kb/1439/kubernetes-operator-cluster-ingress), but now I want to expose things publically to *.aptlab.griffinht.com. but how!??
K8s service account - omnictl service account
This took so long for me to find the docs...
Running kubectl proxy --port 8000 with Traefik config
providers:
kubernetesIngress:
#endpoint: "https://omni.aptlab.griffinht.com:8100"
endpoint: "http://localhost:8000"
api:
insecure: true
log:
level: DEBUG
Let's try a simple ingress.yaml to see if things work.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: foo
spec:
rules:
- host: aptlab.griffinht.com
http:
paths:
- path: /
pathType: Exact
backend:
service:
name: hello-world-service
port:
number: 80
Checking the Trafeik dashboard shows it worked!
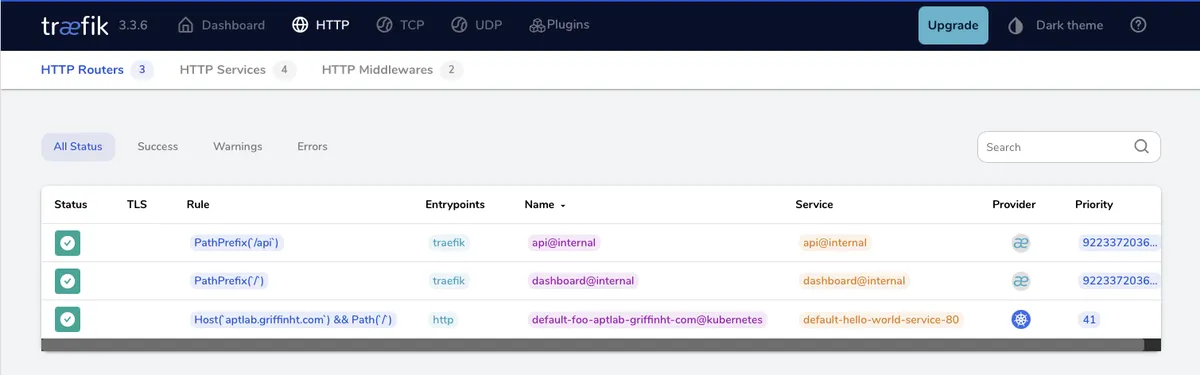
Visiting http://atplab.griffinht.com:80 results in a gateway timeout.
2025-04-26T15:22:01Z DBG github.com/traefik/traefik/v3/pkg/server/service/loadbalancer/wrr/wrr.go:213 > Service selected by WRR: http://10.244.0.53:80
2025-04-26T15:22:31Z DBG github.com/traefik/traefik/v3/pkg/proxy/httputil/proxy.go:121 > 504 Gateway Timeout error="dial tcp 10.244.0.53:80: i/o timeout"
What is 10.244.0.53? It appears to be some kind of internal cluster IP address - when I am in the hello-world pod I can curl 10.244.0.53:80 no problem. Obviously Traefik doesn't have access to this, since it is running on a random virtual machine.
I guess I will have to figure out how to proxy the Traefik VM to my cluster.
part 2
curl 10.244.0.53:80
curl -fsSL https://kubevpn.dev/install.sh | sh
kubevpn connect
This will use our K8s service account from earlier that kube proxy is using.
better solution
Let's just do the proper thing of access the cluster via a Tailscale node in the cluster. I could use the existing Tailscale operator, but I'm not really sure how to configure SUBNET ROUTER thing
I could run tailscale in the cluster, or I could just use the tailscale talos extension
but wait... why not just run traefik in the cluster at this point and vpn to traefik...
even better solution
duh! no more k8s nightmare!